Home | Products| Application Enforcer |Implementing Data Security Using Attribute Based Access Control (ABAC)
Access control systems play a crucial role in maintaining secure IT environments. As your organization grows and evolves, traditional access management methods struggle to meet contemporary demands. This is where Attribute-Based Access Control (ABAC) comes into play, providing a more dynamic, flexible, and scalable approach to managing access to sensitive data and systems.
This white paper explains the benefit of data-centric ABAC, along with best practices to expedite time to market. It also delves into how NextLabs’ solution is designed to enhance organizational agility and leaves the company in a much better position to respond to always-changing business conditions and regulatory environments.
The Challenge of the Extended Enterprise
The “extended enterprise,” which includes customers, devices, and partners, exposes weaknesses in traditional identity and access management (IAM). Organizations need to share critical data internally and externally to optimize productivity and stay competitive, but issues arise due to:
- Data being more accessible to employees and partners
- Difficulty in identifying all authorized users and devices
- Frequent changes in user and partner status, outpacing static systems.
The ABAC Solution
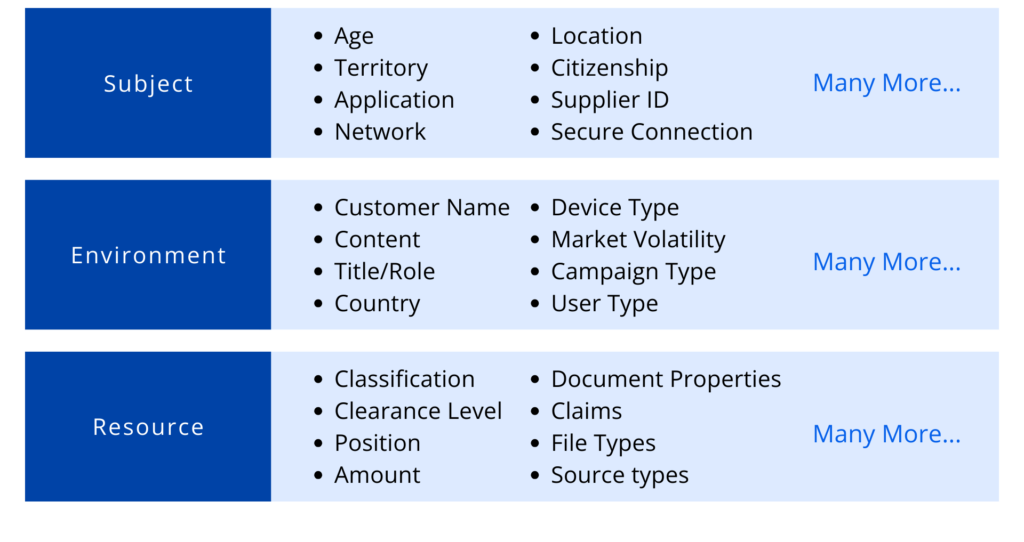
ABAC is a modern access control approach designed to address the limitations of traditional Identity and Access Management (IAM) in current complex business environments. It enables organizations to create dynamic, context-aware policies based on attributes of subject, environments, and resources.
Policies are flexible and reusable across systems and devices. Unlike static permission models, ABAC evaluates access request in real time using attributes from multiple sources, including external ones. It also adapts automatically to risk level.
Implementing ABAC
ABAC relies on several essential inputs to function effectively. For data-centric use cases, three key components are necessary: data classification, identity attributes, and policies. Most organizations already have the processes in place to supply these inputs.
The NextLabs Approach
The NextLabs CloudAz platform was developed to automate these processes, allowing data-centric ABAC policies to be applied centrally throughout the extended enterprise. The tools can be grouped into the following components:
- Business Policy Management – Digitize information sharing requirements as policy, centrally manage and deploy policies
- Attribute Management – Leverage existing attributes, delegate ownership, and define integration points to internal and external attribute stores
- Business Policy Evaluation – Dynamically evaluate data access no matter where data resides, using attributes presented at run-time
- User and Data-Centric Enforcement – Automate user and data-centric information controls
Read the white paper to learn more about ABAC, the complex challenges of the extended enterprise, and the solution that enables real-time authorization and dynamically evaluates information access event by using the most up-to-date information.






