Home | Intelligent Enterprise | Data-Centric Security| How Zero Trust Data Security Can Neutralize the Impact of Ransomware Attack
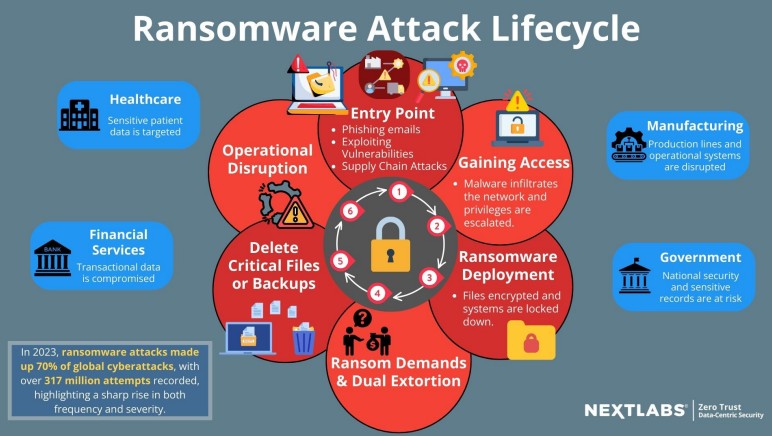
In 2023, ransomware attacks accounted for nearly 70% of global cyberattacks, with over 317 million attempts. These increasingly frequent and sophisticated threats are targeting industries such as healthcare, finance, manufacturing, and government. The increasing attacks is mainly driven by these industries’ reliance on confidential data and critical infrastructure, making them prime targets.
Impacts of Ransomware Attacks
Ransomware attacks have severe financial and operational impacts on organizations. The immediate cost is often the ransom, which can be thousands to millions of dollars. However, the damage extends beyond this, including significant downtime—averaging 24 days—which disrupts operations and affects productivity and customer service. In critical sectors like healthcare and manufacturing, downtime can compromise patient care or halt production, resulting in revenue loss. Stolen data, such as intellectual property or financial records, can lead to competitive disadvantages, legal issues, and reputational damage. To prevent these consequences caused by ransomware attacks, organizations may invest in cybersecurity upgrades, data restoration efforts and patching vulnerability.
Approach to Countering Ransomware Threats
While it’s difficult to completely prevent ransomware attacks, organization could implement a range of protective measures to neutralize their impacts.
- Real-time Verification of User Requests: Using the Zero Trust principle of “never trust, always verify,” organizations can dynamically evaluate user actions and attributes to ensure only authorized users can access sensitive data.
- Digital Rights Management (DRM): DRM provides a robust mechanism to help organizations control how digital files and data are accessed, copied, or shared.
- Externalized authorization: Centralized and real-time policy enforcement ensures consistent access control across applications, enabling immediate revocation of permission when a threat is detected.
- Data obfuscation and encryption: Encrypting data at rest using Format-Preserving Encryption (FPE) ensures sensitive data is unreadable even if stolen.
Solution to Address Ransomware Attacks
NextLabs Zero Trust Data Security combines zero trust principles with data-centric security to limit the scope of ransomware attacks and safeguard critical assets. This approach also ensures business continuity while minimizing operational disruption.
Key Features
- Dynamic Authorization Policy Engine – utilizes Attribute-Based Access Control and Zero Trust Architecture to enforce least privilege access, continuously verify requests, and adapt policies in real – time to mitigate threats.
- Externalized Authorization – offer robust ransomware protection by implementing real-time, Policy-Based Access Control (PBAC).
- Automated and Persistent Rights Protection with Traceability – Data-centric security solution like SkyDRM provides automated, policy-driven protection for unstructured data throughout their lifecycle by enforcing access rights upon upload to any application or file repository.
- Database Operation and Data Manipulation Control – uses attributes-based policies to control Create, Read, Update, and Delete (CRUD) operations across all access points.
- Real-time Data Masking and Obfuscation using Format-Preserving Encryption – leverages Format-Preserving Encryption (FPE) by encrypting sensitive data at rest, ensuring it is unusable if exfiltrated.
- Centralized Management of Policy for Comprehensive Governance – streamlines governance by consistently enforcing security policies, consolidating access data, automating compliance, and enabling quick threat responses through real-time monitoring.
By using the right approach and solution, organizations can thwart ransomware attacks like Sodinokibi (REvil) attack and ensure data protection, business continuity, and regulatory compliance.
For more detailed explanations, examples, use case, download the white paper to explore!






