Traditional security approaches based on static policies and manual access controls are no longer sufficient to ensure adequate protection. Dynamic authorization is essential for securing modern, distributed IT environments because it provides real-time, adaptive access control that is context-sensitive and risk-aware. It allows organizations to better handle increasingly complex access scenarios, offering granular, context-driven access decisions. As businesses move towards cloud infrastructures, remote work, and Zero Trust models, dynamic authorization becomes a vital part of maintaining both security and compliance in a rapidly changing landscape. Dynamic authorization enables the enforcement of policies in real time, allowing organizations to respond quickly to changes in the environment and maintain security.
What is Dynamic Authorization?
Dynamic authorization refers to the real-time process of granting or denying access to resources based on a set of policies, contextual factors, and real-time conditions that can change during the access request process. Unlike traditional access control lists (ACLs) and role-based access control (RBAC) which are based on static authorization that grants access based on fixed roles or predefined permissions, dynamic authorization considers the context, environmental factors, and conditions surrounding the access request, such as the user’s location, time of access, device, behavior patterns, or other factors that may change during a session to make authorization decision. This flexibility allows organizations to apply more granular, flexible, and adaptive security policies.
Key Aspects of Dynamic Authorization:
- Policy-Driven
Authorization decisions follow policies that define conditions for access, evolving with changing circumstances. These dynamic policies assess context and attributes in real-time, adapting based on predefined conditions or past access patterns. This approach improves clarity and reduces errors compared to traditional access controls.
- Adaptive Security
Dynamic authorization policies adapt to changes in user behavior and system conditions, ensuring access remains appropriate. IT systems can adjust permissions in response to threats, such as restricting access if a device is compromised.
- Contextual Decision-Making
Unlike static models like RBAC, which grant access based on fixed roles, dynamic authorization considers context, such as network type, time of access, device security, and action risk. This enables granular control, allowing conditions like “read only from a trusted IP” or “access granted after multi-factor authentication.”
- Real-Time Evaluation
Dynamic authorization policies are evaluated in real-time, considering user, resource, environment, and action attributes. This ensures access decisions use up-to-date information, reducing security risks from outdated permissions.
Why Does Dynamic Authorization Matter?
Dynamic authorization plays a critical role in modern IT environments due to several reasons:
- Increased security and granularity
- Flexibility and adaptability
- Risk-based access control
- Compliance and regulation
- Improved user experience without compromising security
- Zero Trust and adaptive security
- Data-Centric Security
Examples of Dynamic Authorization Use Cases

Using Dynamic Authorization to Implement Policy-Based Access Control
Implementing Policy-Based Access Control (PBAC) using Dynamic Authorization is a highly effective approach to enforce access control policies in real-time, based on a range of dynamic contextual factors. PBAC is essentially an evolution of traditional access control models (like RBAC and ABAC) where access decisions are made based on predefined policies that consider attributes and context rather than just roles or permissions.
How Dynamic Authorization Supports PBAC
Dynamic Authorization enables real-time, context-aware decision making that considers not just the identity of the user (as in RBAC), but also dynamic attributes, environmental conditions, user behavior, and other real-time factors. This aligns perfectly with PBAC, where access decisions are driven by policies based on a combination of attributes and conditions, evaluated at the time access is requested.
Steps to Implement PBAC Using Dynamic Authorization
Here’s a structured approach for implementing PBAC using Dynamic Authorization principles:

Define Policies

Identify Dynamic Attributes for Policy Evaluation
Use a Policy Decision Point (PDP)

Integrate Policy Enforcement Points (PEP)

Continuous Improvement & Optimization

Implement a Risk-Based Access Control Mechanism

Monitoring & Auditing
Example of PBAC with Dynamic Authorization
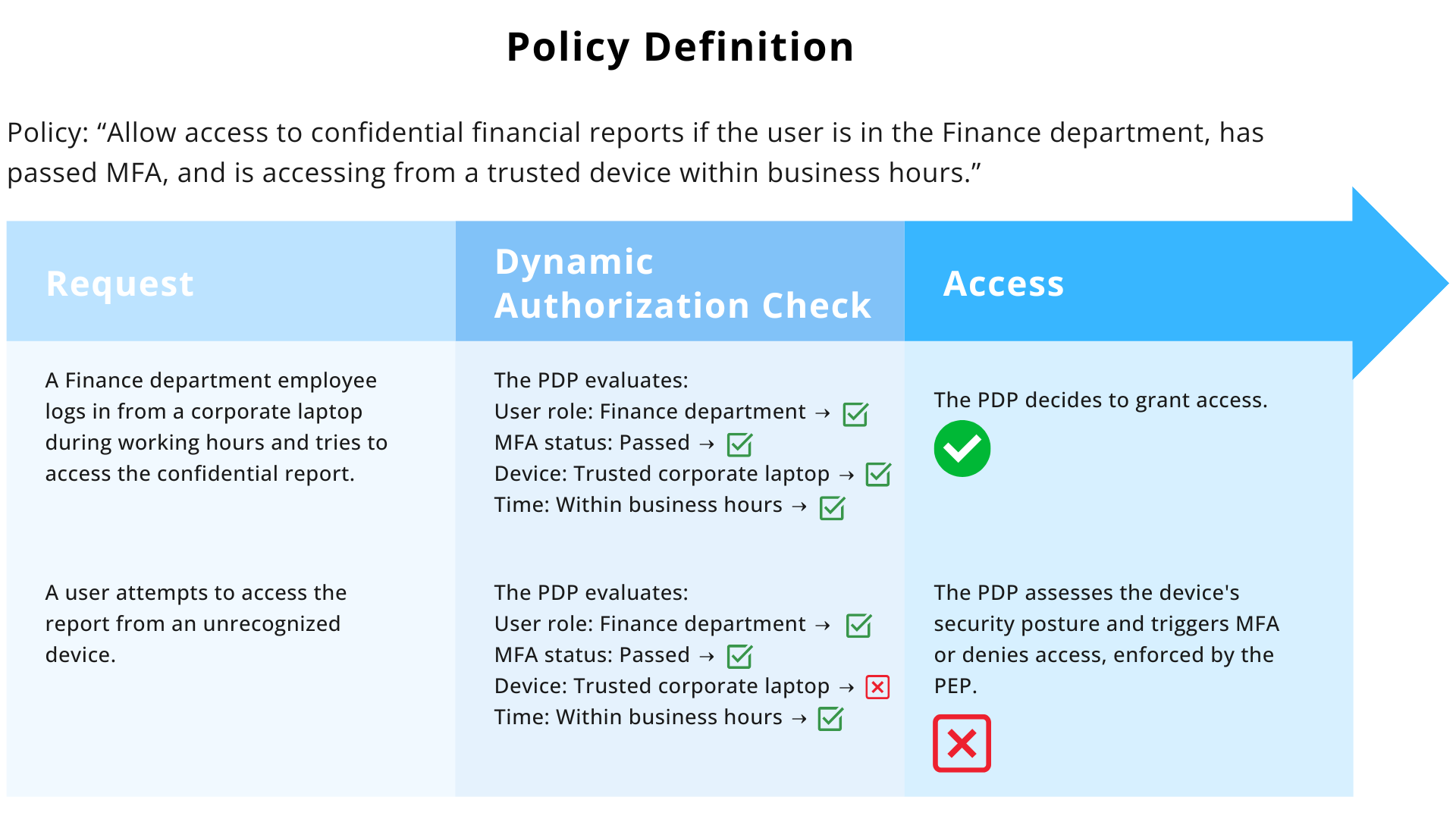
Takeaways
Dynamic Authorization is an essential component in implementing real-time policy enforcement and PBAC because it allows for real-time decision-making based on the attributes and context of the users, resources, and their environment. By using a combination of PAP, PDPs, PEPs, and dynamic policies, PBAC can adapt to changing conditions, ensuring that access is granted or denied based on a comprehensive set of factors rather than static, predefined roles alone.
By combining PBAC and dynamic authorization with robust Identity and Access Management (IAM) practice, organizations can create a more flexible, context-aware, and adaptive authorization system that evaluates access requests based on a wide range of dynamic factors. This approach provides more granular and real-time control over who can access what, when, and under which conditions, significantly enhancing security and compliance. To learn more about dynamic authorization, explore our CloudAz brochure.
- Real-Time Policy Enforcement in Dynamic Environments
- What is Dynamic Authorization?
- Key Aspects of Dynamic Authorization:
- Why Does Dynamic Authorization Matter?
- Examples of Dynamic Authorization Use Cases:
- Using Dynamic Authorization to Implement Policy-Based Access Control
- Example of PBAC with Dynamic Authorization
- Takeaways
- Resources






