Keeping IT resources secure while making them availability and easily accessible is a major challenge for enterprises. With an increasingly sophisticated computing environment, how can enterprises ensure scalable and consistent enforcement of access controls?
Understanding PBAC
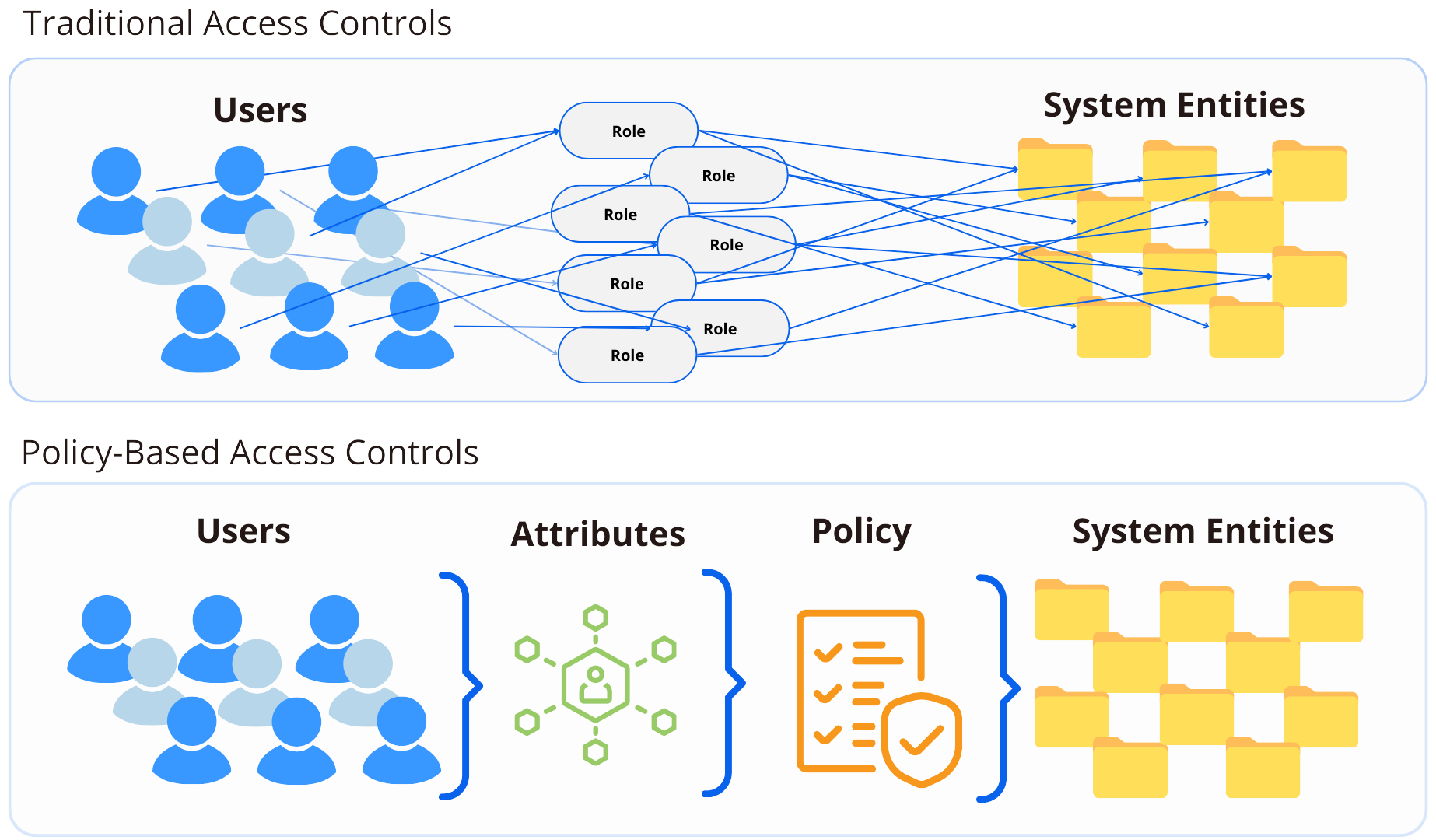
Policy-based access control (PBAC) also known as Policy Based Access Management, is a security model that manages and enforces access to resources based on a set of policies rather than hard-coded rules, static permissions, roles, groups, or user identities alone. In PBAC, access decisions are driven by centrally managed policies that define conditions under which a user or entity is allowed or denied access to resources. By using PBAC, organizations can define, enforce, and manage access in a way that aligns with their business needs, enhances security, reduces administrative overhead, and ensures compliance with regulatory standards. PBAC is particularly useful in dynamic and complex environments where access decisions need to be flexible and scalable.
By using a 3-tier Policy Enforcement Point (PEP), Policy Decision Point (PDP), and Policy Administration Point (PAP) architecture, PBAC allows for efficient and centralized management of complex access control policies across the entire IT landscape. Instead of auditing and modifying roles across the entire organization, PBAC allows quick adjustment of entitlements in response to changes in requirements, ensuring that assets are secured through set rules or policies. PBAC is an adaptable authorization solution because it can support a variety of access points by automating security controls in applications and on data. When PBAC is built with Attribute-Based Access Control (ABAC) support, the approach combines roles and attributes to provide flexible and dynamic access control.
PBAC vs. Traditional Access Controls
Key Characteristics of PBAC
- Policies: These are rules that define what is permissible in the system, often including conditions based on roles, attributes, or other contextual factors. For example, a policy might state, “Only employees in the Finance department can access financial reports after business hours.”
- Granularity: Policies can be very fine-grained, considering various factors such as user roles, time of day, location, device being used, and more.
- Dynamic Control: PBAC allows access decisions to be made dynamically based on real-time contextual information. For example, a user might be granted access to sensitive data if they are accessing it from a company-approved device but denied if they are using a personal device.
- Centralized Management: Policies are often managed centrally, which means administrators can define and adjust access rules for different resources or user groups from one place. This central management makes it easier to update policies and ensure consistency across an organization.
How PBAC Works
Policy Definition
Policies are at the core of PBAC. These are rules that define who can access what resources under what conditions. A policy in PBAC typically involves several factors, such as the user, the resource, the action being performed, and sometimes environmental factors (like time of day or location).
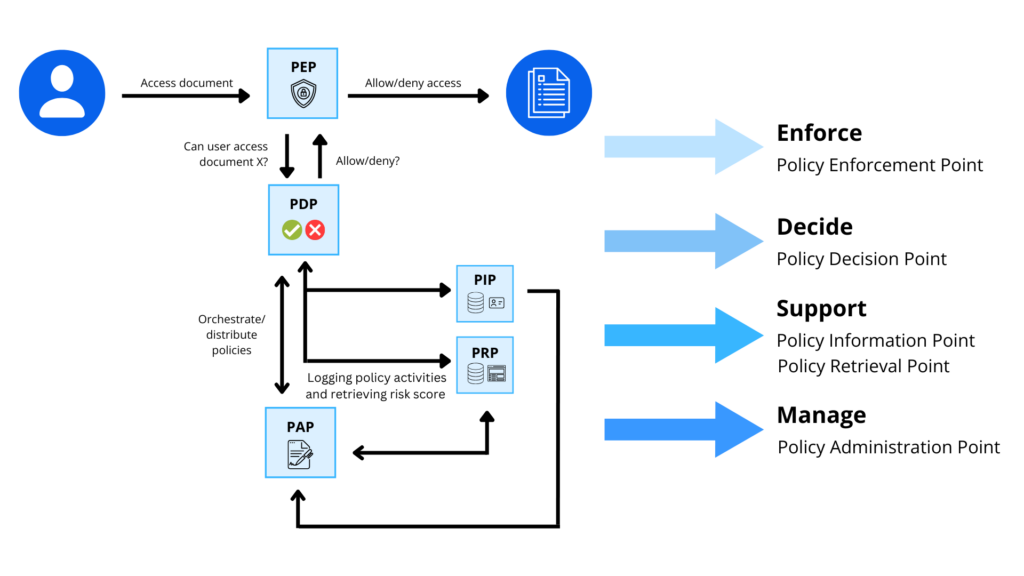
Policy Definition Point (PDP)
The PDP is the component responsible for evaluating access requests against the defined policies. When a user requests access to a resource, the PDP examines the request, retrieves the relevant policies, and makes a decision whether access should be granted or denied.
It evaluates the conditions in the policies based on the user’s attributes (e.g., role, department), the resource’s attributes (e.g., classification, ownership), and the action requested (e.g., read, write).
The PDP returns an access decision to the Policy Enforcement Point (PEP), which implements the decision.
Policy Enforcement Point (PEP)
The PEP is responsible for enforcing the decisions made by the PDP. When the PEP receives an access decision, it either grants or denies access to the user based on that decision.
The PEP could be a web application, API gateway, or any system component that controls access to resources.
Policy Administration Point (PAP)
The PAP is responsible for managing and administrating the policies. It allows administrators to define, update, or delete policies, which are then stored in the policy repository.
The PAP provides an interface for policy management, usually through a centralized management console.
Attributes
Policies in PBAC often use attributes as conditions. These can include:
- User attributes (e.g., role, department, seniority, security clearance).
- Resource attributes (e.g., file type, owner, classification).
- Action attributes (e.g., read, write, delete).
- Environmental attributes (e.g., time of day, location, IP address).
These attributes are typically used in policy conditions to make access decisions more dynamic and fine-grained.
Advantages of PBAC
Data security is no longer just about protecting perimeters or preventing cyberattacks. It is much more about prevent unauthorized access and keeping confidential information safe from authorized users as well, which includes everyone from employees and contractors to third-party vendors and customers, as the enterprise’s entire network is prone to data loss from accidental or malicious leakage. PBAC offers a myriad of advantages:
- Centralized control & management
- Scalability
- Flexibility & granularity
- Improved security
- Adaptability to changing business, compliance, and audit requirements
- Support for complex & hybrid environments
- Reduced complexity over time
- Better decision-making
- Support for delegated administration
More Information
For more information on NextLabs PBAC solutions, read the full whitepaper or watch Control Center Policy Authoring: Nextlabs Policy-Based Authorization Management and Control Center Administration Section- NextLabs Policy-Based Authorization Management.






