Home | Intelligent Enterprise| Zero Trust Architecture | Implementation of a Zero Trust Architecture
Zero Trust has become a leading cybersecurity approach, emphasizing the “never trust, always verify.” Yet, implementation remain challenging.
The NIST National Cybersecurity Center of Excellence (NCCoE) has released a detailed guide on implementing Zero Trust Architecture (ZTA). This guide illustrates proposed architectures for both on-premises and cloud environments that incorporate the ZTA characteristics outlined in NIST SP 800-207. While the specifics of ZTA implementation may differ from one organization to another—and even among various groups within the same organization—there are universal principles that should inform any implementation.
This whitepaper dives deeper into models and reference architectures from agencies like CISA and the Department of Defense, highlighting common requirements for successful ZTA adoption across organizations.
Using the NIST Cybersecurity Framework to Guide ZTA Implementation
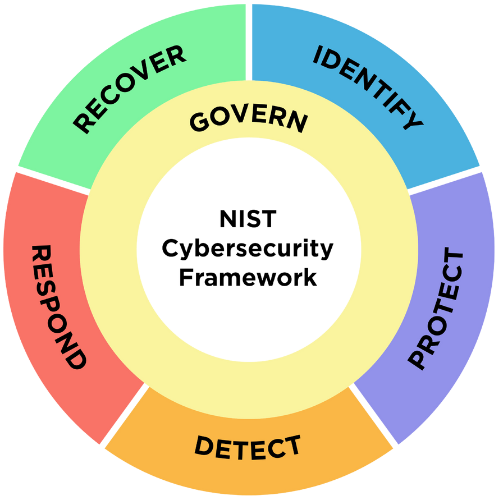
The NIST Cybersecurity Framework (CSF) 2.0 provides a comprehensive approach to managing and mitigating cybersecurity risks for organizations, offering guidance that the principles of Zero Trust complement. The framework’s core functions: Identity, Protect, Detect, Respond, and Recover.
- Identity: understanding and managing cybersecurity risks to systems, assets, data, and capabilities.
- Protect: implementing safeguards to ensure the delivery of critical services and the protection of assets.
- Detect: identifying the occurrence of cybersecurity events promptly
- Respond: having response plans and procedures in place to address security incidents promptly.
- Recover: implementing backup and recovery processes and ensuring business continuity.
Each function supports ZTA adoption by ensuring visibility across assets, proactive threat detection, and structured response to incidents.
CISA’s Five Pillars of Zero Trust
CISA’s Zero Trust Maturity Model outlines five key pillars and three cross-cutting capabilities critical for utilizing ZT principles within organizations.
- Identity: secure verification of users, devices, and systems via MFA and least-privilege access.
- Devices: implementing endpoint protection, device management, and continuous monitoring
- Network: network segmentation and micro-segmentation to limit threat movement.
- Applications & Workloads: enforcing secure coding, vulnerability assessments, and runtime protection
- Data: encryption, DLP, and classification to secure data throughout its lifecycle.
Three cross-cutting capabilities focuses on Visibility, Automation, and Analytics ensuring ongoing monitoring and adaption. By incorporating these pillar and cross-cutting capabilities into cybersecurity strategies, organizations can establish a comprehensive Zero Trust framework to reduce risk and enhance cyber defense posture.
United States Department of Defense Zero Trust Reference Architecture
The DOD ZTRA expand upon seven key pillars: Identity, Devices, Network, Data, Applications & Workloads, Visibility & Analytics, and Automation & Orchestration. Each pillar plays an important role in implementing Zero Trust principles effectively within the DoD’s environment.
Key Elements of a Zero Trust Architecture Implementation
Indeed, any Zero Trust Architecture will also include the following components:
- Policy Administration Point (PAP) – defines and manages security policies
- Policy Decision Point (PDP) – evaluates access requests and makes allow/deny decisions
- Policy Enforcement Point (PEP) – applies and enforces decisions in real-time.
- Policy Information Point (PIP) – provides a bridge between the PDP and the values of the subject, data, and environmental attributes used to define policies in the PAP
Together, these components create a continuous cycle of evaluation, enforcement, and governance that strengthens security posture and supports regulatory compliance.

The NextLabs Approach
NextLabs offers a unified Zero Trust policy management solution that operationalizes all key elements of ZTA to provide fine-grained access control, real-time request evaluations, and supports effective policy governance and robust identity management. This platform enables organizations to dynamically enforce data access controls, ensuring compliance with least privilege principles and enhancing cybersecurity resilience.
Interested to learn more?






